IT Security in the Workplace
IT Security in the Workplace

IT security at the University of Oldenburg is not the sole responsibility of the IT department or informationsecurity management. Every member of the university can help to ensure that IT security is maintained.
After all, it is all of you who thwart attempts by attackers to gain access data through phishing emails or to prevent unauthorised access through complex passwords.
You can find out how to recognise dangers and how to arm yourself against them on this page.
Recognising and avoiding phishing
What is phishing?
Attacks against companies and universities are now regularly initiated by phishing emails. Users of the University of Oldenburg also regularly receive such emails.
The fake emails are designed to trick you into entering your login details on a fake website or opening an attached file with a virus.
The following points will help you recognise phishing:
- Look out for the indication that an email is coming from an external source.
- Check whether a fake sender address is being used.
- The text of the email indicates an urgent need for action, for example: "If you do not update your data immediately, it will be irretrievably lost ...".
- Threats are used: "If you do not do this, we will unfortunately have to block your account ...".
- You are asked to disclose confidential information or enter login details.
- The email contains links or forms.
- The email appears to come from a known person or organisation, but the sender's request seems unusual.
Does this email really come from "above"?
CEO fraud is a type of fraud in which someone poses as a university executive and attempts to trick employees into handing over confidential information or transferring money to a specific bank account.
The fraudster may make contact with the victim by email, telephone or other means of communication and pretend to be a trustworthy person. This type of fraud is particularly dangerous as the fraudsters are usually very well prepared and present themselves very convincingly. They use various techniques to gain trust and obtain information.
To protect yourself, you should always be careful when you are contacted by people claiming to be a superior or manager and check carefully whether the enquiry really comes from a trustworthy source.
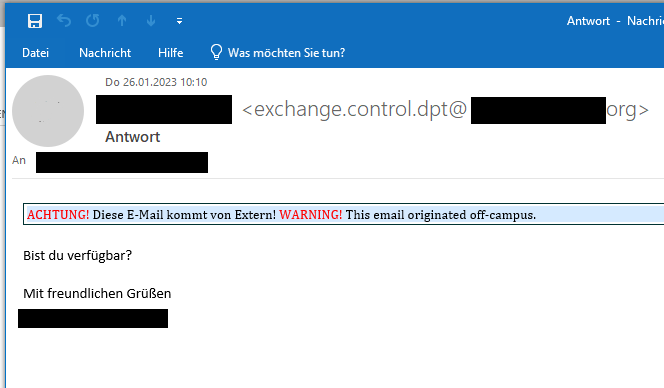
Often, a short email purporting to be from someone at the university will only ask if you are available. If you reply, the scam begins.
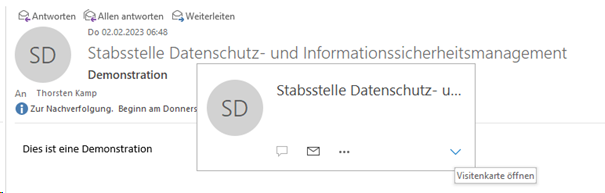
How to check the sender of an email
To check the sender's email address in the email client, hover over the sender in the email and then click on the small arrow to open the contact field.
The sender's address will now be displayed.
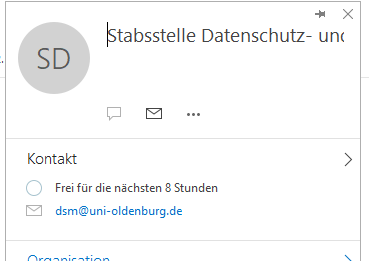
Pay attention to the part after the @ sign. This is the sender domain. The part with the last dot (".") is important.
Example:Max.mustermann@uni-o1denburg.de does not come from the University of Oldenburg, there is a "1" instead of an "l" in the sender address.
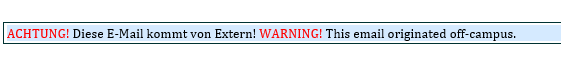
Attention! This email comes from an external source
Pay attention to whether there is a note at the beginning of the email indicating that it comes from an external source.
You can often recognise fraudulent emails this way.
Pay attention to attachments
If you are not expecting an attachment, you should be particularly sceptical. The senders of phishing emails often join in an existing conversation and send a supposed reply with a virus file or a link to a virus.
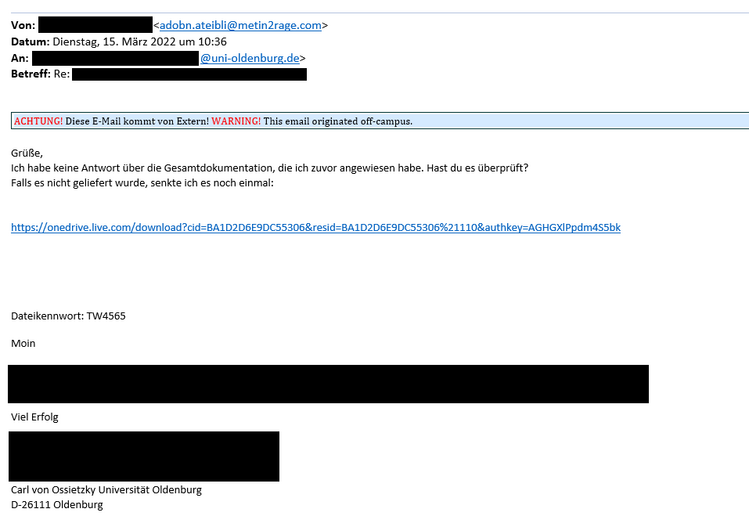
Distrust links
Check whether a link in an email is safe. Move the mouse pointer over this link in your email without clicking on it. Now you can see where the link actually leads to:
Ignore the beginning (http:// or https://). Then read up to the first "/". The part before the "/" with the dot "." shows the actual destination of the link. The following link leads to "ntmov.com" not to the University of Oldenburg: https://www.ntmov.com/img/cas01.elearning.uni-oldenburg.de.htm
Do not trust requests to log in
If you are unexpectedly asked to log in to a website in an email, never click on the link. Open a web browser and type in the internet address you recognise manually.
What to do if you suspect phishing
If an email seems suspicious to you and you suspect phishing, for example,
- If necessary, first move the email to the Junk email folder so that all links and other automated functions are automatically blocked.
- Ask the sender to confirm its authenticity in person/by telephone.
- If you have any suspicions, forward the email to IT services for checking:
- Open a new email,
- enter "Please detect this as spam" as the subject,
- drag and drop the email in question into this new email and send it to SPAM-Verdacht@uol.de and to dsm@uol.de.
Secure handling of passwords
Use secure passwords
Secure passwords are passwords that are difficult to guess. Here are a few tips for creating a secure password:
- Use a combination of upper and lower case letters, numbers and special characters.
- Use at least 8 characters.
- Avoid words that can be found in the dictionary.
- Avoid information that is easily accessible (e.g. date of birth, names of family members).
How can you memorise a secure password?
Use a sentence: Think of a sentence that you can remember and use the first letters of each word as your password.
Use a password manager: A password manager can generate and store secure passwords for you. The best-known password safes include the programme Keepass (keepass.info/) and the offshoot KeepassXC (keepassxc.org/). IT services can help you with the installation.
Handling sensitive data
Do not store sensitive data on unprotected devices
Save your data on the central servers, e.g. your L drive, or in the university's own cloud (https://cloud.uol.de).
Do not save official data on USB sticks.
Use secure transmission methods when transferring confidential data
Do not send confidential data unsecured by email. You can exchange data via the university's own cloud (https://cloud.uol.de). You can find instructions at IT services
Or at least use a ZIP archive with a password. If you need to exchange data regularly, you should agree a secure encryption method with the recipients.
Close security gaps
Keeping software and systems up to date
Update, patch, refresh or bugfix - what is it? - These terms ultimately refer to the same process: manufacturers eliminate errors, close security gaps or add functions without having to reinstall the software.
Security vulnerabilities are weak points in software that allow attackers, for example, to introduce malicious programmes and take control of other people's systems. It is a perpetual race: Hackers discover vulnerabilities, manufacturers close them as quickly as possible. The hackers find them again and it's back to the manufacturers.
This is why it is so important to keep software and systems up to date and minimise vulnerabilities in order to offer hackers as few opportunities for attack as possible.
Therefore, remember to install updates regularly if you use self-installed applications on your system.
Even if your Windows computer reports that updates are available, you should install them as soon as possible.


