ICBM-IT
Please always send enquiries to ICBM-IT via email to
- these will only be read by the team members named on the left.
Latest news from ICBM-IT
Message from Renke Schütte (05.06.2024):
Dear colleagues,
Our university is currently under increasing attack again. Once again, the attackers have succeeded in gaining access to user accounts, once again the attackers have gained access to our secure, internal area and are up to mischief there.
The newer SentinalOne anti-virus software has succeeded in neutralising some of the programmes used by the attackers to spy on other passwords, among other things.
Based on the experience of past attacks by SentinalOne /Thor, I believe there is hope that we will get off lightly again, but there may be operational restrictions due to defence measures taken by IT services.
My request:
- Be vigilant so that your access data does not fall into unauthorised hands.
- Use long, complex passwords! Passwords of only 8 characters without numbers, special characters or capitalisation are unsuitable.
If you still have a weak password, change your password immediately! The use of simple passwords is negligent!
You can change your password now here: https://pw.uol.de/
- NOBODY from IT services or other authorised persons will ask you for your access data including your password. For this reason: Do not tell your password to anyone else.
- Only use software from really trustworthy sources, there are thousands of software packages floating around on the Internet that steal passwords or compromise our computers, steal data, etc. If you are not 100% sure, do NOT install such software (note: always pay attention to the licence terms for software, software is often free for private use, but requires a licence and costs money in a university environment).
- Do not download anything from websites where you are not sure that the site and its contents are secure and trustworthy.
Mission statement
We are service-oriented contacts for all questions and problems in the area of IT infrastructure. We see our central tasks in
- advising on the purchase of IT hardware and the use of central IT services at the university,
- setting up and maintaining an operational software environment,
- monitoring and analysing the IT infrastructure in order to avoid problems in advance and ensure security, and
- providing support for IT solutions to questions of scientific computing and data management as well as online teaching and presentation technology.
Our goals are good communication and transparency as well as sustainable solutions and security.
How do I get support?
Please always send your request by email to (ticket system). You will receive an email reply as soon as possible from the IT team member who has dealt with your request. To prioritise requests that arrive at the same time, please describe the importance and urgency of your request in your request.
Be aware of phishing mails
Just some Links:
- BSI Phishing erkennen
- Phishing im Netz erkennen und vorbeugen
- UOL- DSM FAQ
- Verbraucherzentrale Phishing erkekennen
Und doch noch mal ein eigener Text:
Due to recent incidents we would like to remind you how to take care of spam and phishing mails.
Since even in hacker circles there is a shortage of skilled workers, most spam/fraud is not too intelligent (=dangerous), but thanks to DeepL and ChatGPT at least it looks not that bad anymore. That means it's getting more difficult to detect, On the other hand: looking at the mail is usually still without danger and most of the time clicking on links is not harmful either. Entering anything on the linked pages is FATAL in case of a phishing site.
There are a few basic rules you should follow within EVERY mail:
No matter where the mail comes from and in which program you look at it: BEFORE you click on any link, look in the mails header for the full sender (if you can see it) but that's just a first clue. After that, look at the exact link you want to click on. To do so hover your mouse over the link and the real destination should usually be displayed in the lower left corner (on cell phones, usually long-click the link). After you have clicked on a link, look at the top of the browser address page to see if this is really the institution you want to go to. A few examples to try out:
ICBM IT
ICBM IT
„https://uni-oldenburg.de∕.si42.de/icbm”
None of these links directs to an ICBM or other university page! Last one has to be copied by hand, but obviously it is 'uni-oldenburg.de' between the first slashes after https ;)
This practice of checking links BEFORE and AFTER clicking also applies to clicking links in web pages.
How do I set up a Teams account?
- Instructions for setting up MS Teams (as part of Office365) at university account level can be found at: Register Microsoft account for Teams ...
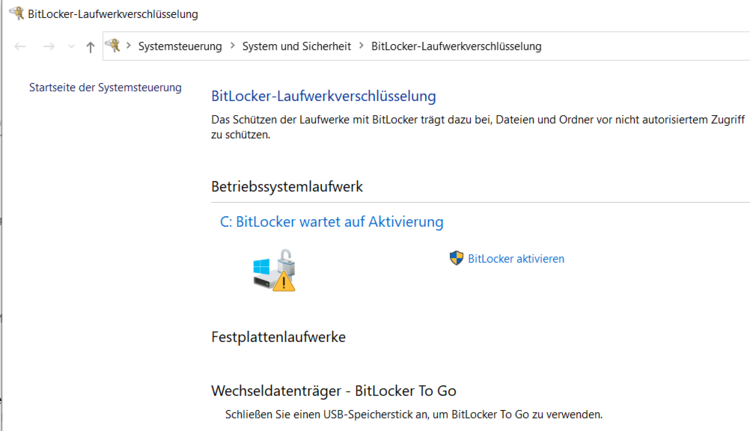
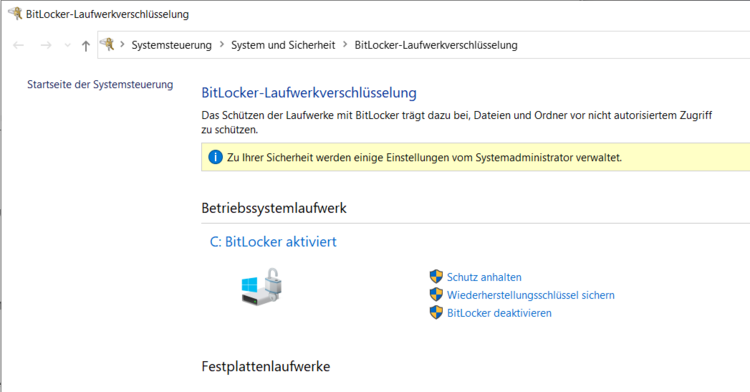
Windows: Is my Bitlocker active?
Bitlocker is a programme to further protect unauthorised access to hard disk data. Normally, this protection is completely unnoticed, but under some conditions a Bitlocker key file is required. If this is not present, access to the data is no longer possible or at least considerably more difficult...
Please check if the Bitlocker is active and inform us if it is by following the steps below:



![[Translate to English:]](/f/5/_processed_/3/2/csm_ICBM-Logo-transparent-_91fe1c6774.png)

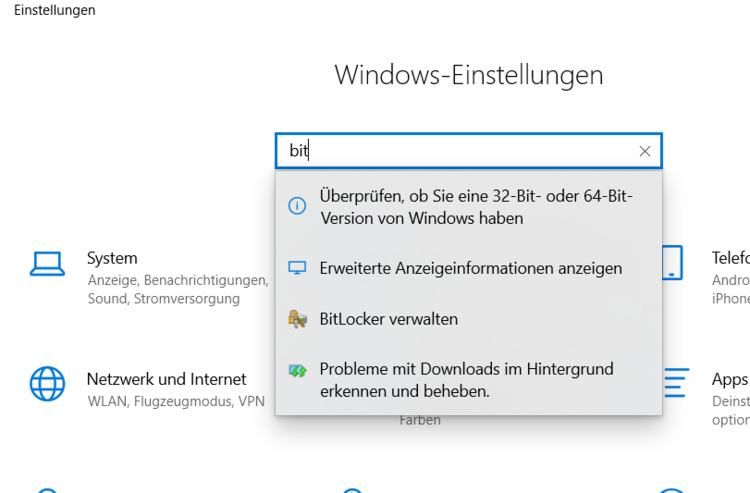
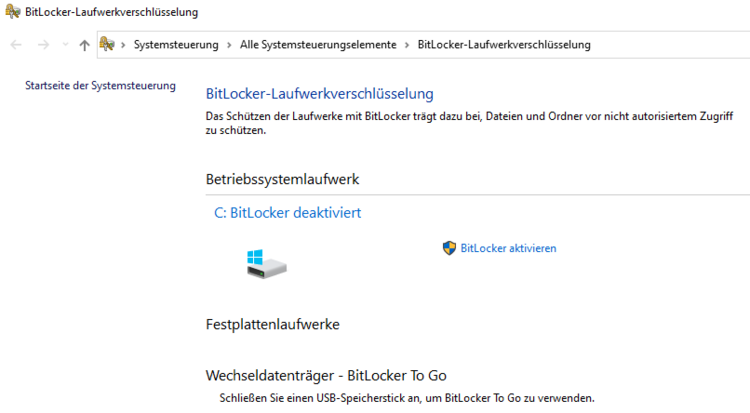 . or
. or