FAQ Data protection and information security
FAQ Data protection and information security
Data protection is an increasingly important issue. But the security of information in general is also an important concern for the university. However, the subject matter is also quite complex. For this reason, you will find an overview of the most important questions and their answers relating to data protection and information security in relation to typical activities at the University of Oldenburg.
Much is regulated in the General Data Protection Regulation (GDPR). The GDPR is an EU regulation that came into force on 25 May 2018. It contains a number of provisions and requirements for the protection of personal data that must also be observed by the university. You can find out here which provisions of the GDPR must be observed in everyday working life and how you can protect data as well as possible against unauthorised access.
You can find further information at Working in compliance with data protection and IT security in the workplace.

The GDPR in everyday working life
You can find out which general provisions of the GDPR must be taken into account in your day-to-day work, which rights data subjects have and which data must be specially protected here.

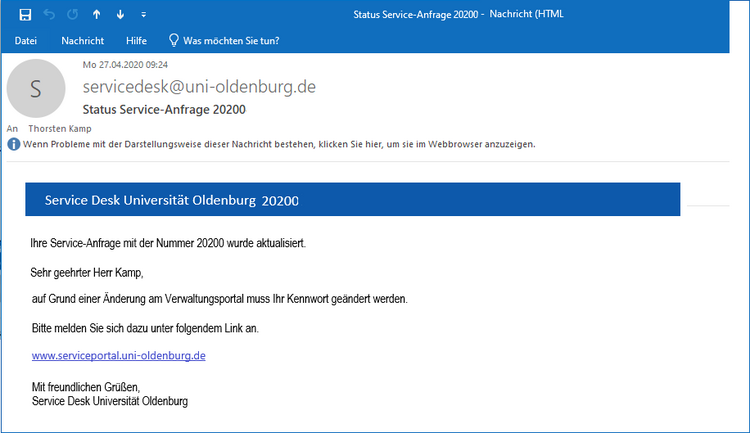
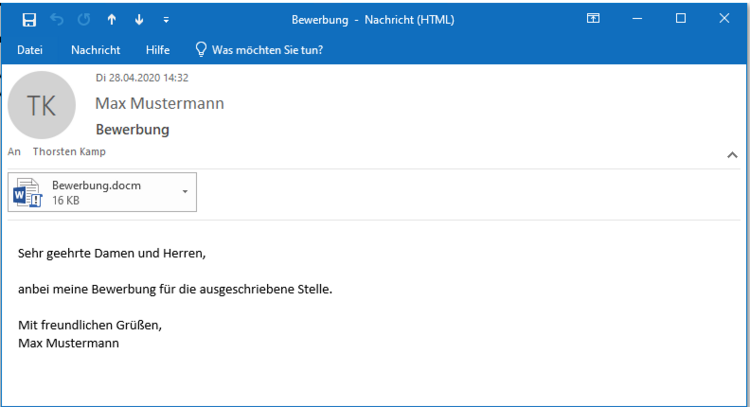
Data protection in email correspondence
Email addresses are always personal data, which is why the GDPR must also be observed here. You can find out what you should consider when dealing with emails here.

Social media, Academic Cloud etc.
The use of various apps and services is often questionable in terms of data protection law. You can find out which services you can and cannot use at the university here.

IT security
Nowadays, the protection of sensitive data always includes measures that specifically secure digital data or make unauthorised access more difficult or, at best, prevent it. You can find out what measures you can take here.

Special requirements in research
Research often involves working with personaldata. You can find out what you need to bear in mind when conducting web-based surveys, for example, or what anonymised data is here.

Photos, notices, paper documents
There are other areas in which the rights of others must be protected, e.g. the "right to one's own image", protection of analogue personal data, etc. You can find out how to act in compliance with data protection regulations here.